Kaspersky ICS CERT Report: 2020 attacks target suppliers of equipment and software for industrial enterprises
卡巴斯基ICS CERT报告:2020年攻击目标为工业企业的设备和软件供应商
In early 2020, a series of targeted attacks on industrial organizations in various regions was reported. According to the latest Kaspersky ICS CERT findings, these hits were focused on systems in Japan, Italy, German and the UK and targeted suppliers of equipment and software for industrial enterprises. Research has shown that attackers used malicious Microsoft Office documents, PowerShell scripts and several other techniques to make it difficult to detect and analyze their malware. One such technique is steganography, a data-hiding technology that conceals messages within digital files.
2020年初,报告了不同地区工业组织的一系列针对性攻击。根据卡巴斯基ICS CERT的最新调查结果,这主要集中在日本、意大利、德国和英国的系统上,目标是工业企业的设备和软件供应商。研究表明,攻击者使用恶意的Microsoft Office文档、PowerShell脚本和其他一些技术,使得检测和分析他们的恶意软件变得困难。这样的技术叫隐写术,一种将信息隐藏在数字文件中的数据隐藏技术。
Targeted attacks on industrial objects organically attract attention from the cybersecurity community as they are sophisticated and focused on sectors that are of critical value. Any disruption in the continuity of work can lead to unwanted consequences from successful industrial espionage to comprehensive financial losses.
对工业目标的定向攻击有组织地吸引了网络安全界的注意力,因为它们非常复杂,而且集中在具有关键价值的部门。工作连续性的任何中断都可能导致从成功工业间谍活动到全面财务损失的不良后果。
This examined series of attacks was no exception. Phishing emails, used as the initial attack vector, were tailored and customized under the specific language for each specific victim. The malware used in this attack performed destructive activity only if the operating system had a localization that matched the language used in the phishing email. For example, in the case of an attack on a company from Japan, the text of a phishing email and a Microsoft Office document containing a malicious macro were written in Japanese. Also, to successfully decrypt the malware module, the operating system must have had a Japanese localization.
经过审查的一系列攻击也不例外。用作初始攻击媒介的网络钓鱼电子邮件是根据每个特定受害者的特定语言量身定制的。只有当操作系统的本地化与网络钓鱼电子邮件中使用的语言相匹配时,此攻击中使用的恶意软件才会执行破坏性活动。例如,在一家日本公司遭到攻击的情况下,网络钓鱼电子邮件的文本和包含恶意宏的Microsoft Office文档都是用日语编写的。此外,要成功解密恶意软件模块,操作系统必须具有日语本地化。
Closer analysis has shown that attackers used the Mimikatz utility to steal the authentication data of Windows accounts stored on a compromised system. This information can be used by attackers to gain access to other systems within the enterprise network and develop attacks. This is particularly dangerous when attackers gain access to accounts that have domain administrator rights.
进一步的分析表明,攻击者使用Mimikatz实用程序窃取了存储在受感染系统上的Windows帐户的身份验证数据。攻击者可以利用这些信息来访问企业网络中的其他系统并发起攻击。当攻击者获得对具有域管理员权限帐户的访问权限时,这尤其危险。
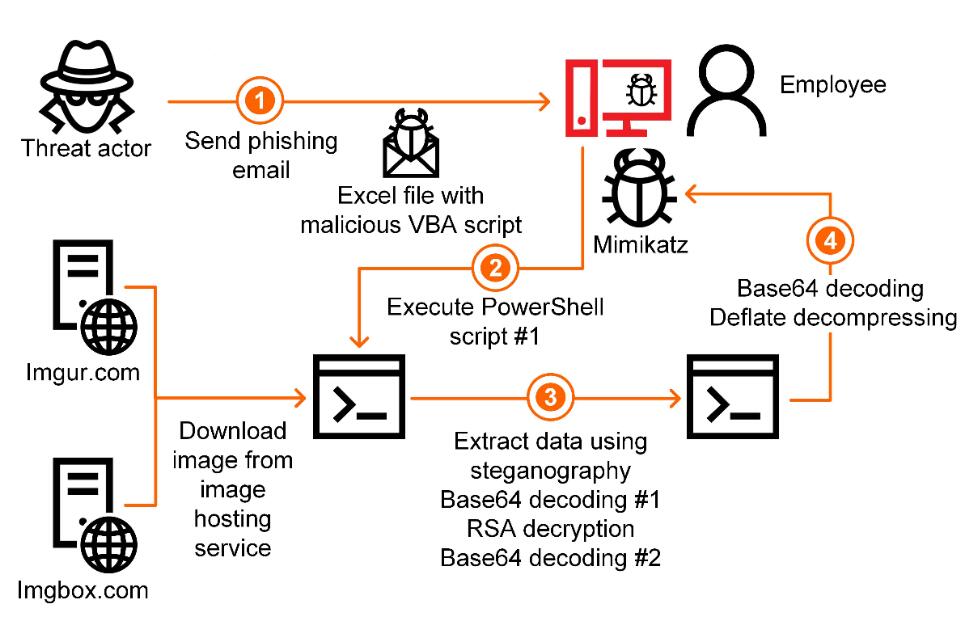
详细攻击方案
In all detected cases, the malware was blocked by Kaspersky security solutions which prevented the attackers from continuing their activity. As a result, the ultimate goal of the criminals remains unknown. Kaspersky ICS CERT experts continue to monitor new, similar cases. If an organization encounters such an attack, it can be reported by using this special form on the Kaspersky website.
在所有检测到的案例中,恶意软件均被卡巴斯基安全解决方案阻止,从而阻止攻击者继续其活动。因此,罪犯的最终目标仍然不明。卡巴斯基ICS CERT专家将继续监控类似新案例。一旦组织遇到此类攻击,可以通过卡巴斯基网站上的此特殊表格进行报告。
“This attack attracted attention due to several, non-standard technical solutions used by the attackers,” said Vyacheslav Kopeytsev, a security expert at Kaspersky. “For instance, the malware module is encoded inside the image using steganography methods, and the image itself is hosted on legitimate web resources. This makes it almost impossible to detect the download of such malware using network traffic monitoring and control tools. From the point of view of technical solutions, such activity does not differ from the usual access given to legitimate image hosting. Coupled with the targeted nature of infections, these techniques indicate the sophisticated and selective nature of these attacks. It is a matter of concern that industrial contractors are among the victims of the attack. If the authentication data of employees of the contractor organization falls into malicious hands, this can lead to many negative consequences, starting with the theft of confidential data and ending with attacks on industrial enterprises through remote administration tools used by the contractor.”
卡巴斯基安全专家Vyacheslav Kopeytsev表示:“由于攻击者使用了几种非标准的技术解决方案,这种攻击引起了人们的注意。例如,使用隐写方法将恶意软件模块编码在图像内部,并将图像本身托管在合法的Web资源上。这使得几乎不可能使用网络流量监视和控制工具来检测此类恶意软件的下载。从技术解决方案的角度来看,这种活动与对合法映像托管的通常访问没有区别。结合感染的针对性,这些技术表明了这些攻击的复杂性和选择性。令人担忧的是,工业承包商是袭击的受害者。如果承包商组织员工的身份验证数据落入恶意人员手中,则可能导致许多负面后果,首先是盗窃机密数据,最后是通过承包商使用的远程管理工具对工业企业发动攻击。”
“The attack on contractors once again demonstrates that for electric power facilities to be operated reliably, it is critically important to ensure workstations and servers are protected – both on corporate and operational technology networks,” comments Anton Shipulin, solution business lead, Kaspersky Industrial CyberSecurity. “Although strong endpoint protection may be enough to prevent similar attacks, in this case, we still recommend using the most comprehensive approach to support the industrial facility’s cyber-defense. Attacks through contractors and suppliers can have completely different entry points within the enterprise, including ones on the OT network. Even though the attack’s objectives remained unclear, it is more accurate to follow the assumption that attackers have the potential to gain access to the facility’s critical systems. Modern means of network monitoring, anomaly and attack detection can help to detect signs of an attack on industrial control systems and equipment in a timely manner, and prevent a possible incident."
卡巴斯基工业网络安全解决方案业务负责人Anton Shipulin表示:“对承包商的攻击再次表明,要让电力设施可靠运行,确保工作站和服务器受到保护至关重要,无论是在企业网络还是在运营技术网络上。虽然强大的端点保护可能足以防止类似的攻击,但在这种情况下,我们仍然建议使用最全面的方法来支持工业设施的网络防御。通过承包商和供应商进行的攻击在企业内部可能有完全不同的入口点,包括在OT网络上的入口点。尽管攻击的目标仍不清楚,但假设攻击者有潜力获得对该设施的关键系统的访问权限,则更为准确。现代的网络监视,异常和攻击检测手段可以帮助及时发现对工业控制系统和设备的攻击迹象,并防止可能的事件发生。”
To reduce the risks of being attacked, industrial organizations are advised to:
- Provide training to employees of enterprises on how to work with email securely and, in particular, identify phishing emails.
- Restrict the execution of macros in Microsoft Office documents.
- Restrict execution of PowerShell scripts (if possible).
- Pay particular attention to PowerShell process startup events initiated by Microsoft Office applications. Restrict programs from receiving SeDebugPrivilege privileges (if possible).
- Install a security solution for corporate endpoints such as Kaspersky Endpoint Security for Business, with the ability to centrally manage security policies, and maintain up-to-date antivirus databases and software modules for security solutions.
- Use security solutions for OT endpoints and network such as KICS for Nodes and KICS for Networks to ensure comprehensive protection for all industry critical systems.
- Install security solutions on all systems with the ability to centrally manage security policies, and maintain up-to-date antivirus databases and software modules for security solutions.
- Use accounts with domain administrator rights only when necessary. After using such accounts, restart the system where authentication was performed.
- Implement a password policy with requirements for the level of complexity and regular password changes.
- Upon an initial suspicion that systems are infected, perform an antivirus check and force password changes for all accounts that were used to log in on compromised systems.
为了降低被攻击的风险,建议工业组织:
- 为企业员工提供如何安全使用电子邮件的培训,尤其是识别网络钓鱼电子邮件。
- 限制Microsoft Office文档中宏的执行。
- 限制执行PowerShell脚本(如果可能)。
- 特别注意由Microsoft Office应用程序启动的PowerShell进程启动事件。限制程序接收SeDebugPrivilege特权(如果可能)。
- 为企业终端安装安全解决方案,如卡巴斯基企业终端安全软件,能够集中管理安全策略,并维护最新的防病毒数据库和安全解决方案软件模块。
- 使用针对运行点端点和网络的安全解决方案,例如针对节点的KICS和针对网络的KICS,以确保对所有行业关键系统的全面保护。
- 在所有系统上安装安全解决方案,能够集中管理安全策略,并维护最新的防病毒数据库和安全解决方案软件模块。
- 仅在必要时使用具有域管理员权限的帐户。使用这些帐户后,重新启动执行身份验证的系统。
- 实施密码策略,并对复杂性和定期密码更改提出要求。
- 初步怀疑系统受到感染时,执行防病毒检查,并强制更改用于登录受感染系统所有帐户的密码










 经营性网站备案信息
经营性网站备案信息 ICP经营许可证
ICP经营许可证 营业执照副本
营业执照副本 不良信息举报中心
不良信息举报中心